Introduction
Good security practice for individuals is still something that most people don’t do, sometimes because people see it as too much additional effort or because people don’t realise the importance of cyber security and what consequences can come from a lack of it. In this post, we’ll look at the importance of a specific good practice that everyone should follow, specifically the use of password managers. Not only does this help secure a user’s online accounts at home, but also an important step that businesses should be taking to ensure their employee’s weak passwords are not a threat to their business.
Good Password Management
Weak and reused passwords are normally the common mistake most people make when securing their online identities. Creating passwords which are easy to remember can be hard and people tend to go with something meaningful to them, such as their pets name and the year they were born (or similar). With the amount of information people put online with today’s social media, things like pets names and birth years can be easy for attackers to find just by looking at someone’s public pages. With lots of websites asking users to constantly change their password as well as adhering to specific password requirements (often making long and complex values), this makes them hard to remember. This is what ultimately leads people to using the same password for multiple sites, meaning once an attacker guesses one they can gain access to all.
Passwords using details unique to you, like your pet’s name, or child’s name (etc) makes it easy for an attacker to just guess what your passwords might be. It’s even worse when using common passwords like “letmein”, “qwerty”, the beloved “password” or “p@ssw0rd!”. These are the easiest for attackers to guess as these are found in common password lists. We’ll touch on these wordlists shortly. As you might have guessed, the best way to solve the problem of weak passwords is by using a password manager. The idea behind using a password manager is you have one very strong password you have to remember. This unlocks the password manager which then stores all you’re passwords, encrypted within, so you don’t need to remember them. Since you don’t need to remember all but your password managers master password, credentials for identities and sites you use can be secure by being made of completely random letters, numbers and symbols. As well as being as long as the website you’re using will allow, normally 64 characters or more. This makes passwords impossible to guess and extremely difficult to crack.
How Do Attackers Get Your Password?
We’ve already mentioned a few things in this post of ways attackers get your password, let’s touch on these here. Knowing how attackers get your online credentials can help you to secure your accounts, and hopefully stop attackers making you their next target.
Social Engineering - Social Engineering is when attackers try to get information out of a human by pretending to be someone else, for example, they may call you on the phone pretending to be your energy or phone provider. They will attempt to steal money, or ask you security questions to find your common answers to questions such as your “mother’s maiden name” or the “place you were born”. If in doubt, always hang up and call the company back on a number you find from their official sources (contact page on their website, for example). Social engineering can also include OSINT (Open source intelligence) practices such as scraping your online social media profiles for information that might make up your password like your pets names, hobbies, sports teams, birth year or family members’ names. It can also be a good idea to use random answers to recovery questions. This will make it harder for attackers to go through account recovery with details they find out about you to gain access to your accounts. This is made easier with a password manager as you can store these answers so you don’t forget them yourself.
Phishing - Phishing comes in a couple of different varieties, but this is when an attacker again pretends to be someone they are not. This commonly happens via text or email and redirects to a fake login page where the victim will enter their login details. These are then sent straight to the attacker. With this in mind, always check links before you click them, if you are unsure navigate to the company’s website directly rather than clicking email links. Remember, scams often use language provoking urgency to make users panic and click the link to log in quickly.
Previous Attacks - When attackers break into company systems they often steal database information containing usernames and passwords and publish this on the internet, either for a fee or free. This information can then be used by other attackers. This is why it’s a good idea to not use the same password for multiple sites, as if one site is breached the email and password combination might already be on the internet for others to try. https://haveibeenpwned.com/ is a good way to sign up for alerts if your email is found in these data dumps. It can also be used to check if a password you use is already in one of these dumps.
Wordlists and Brute Force - Wordlists are created by attackers and contain lots of commonly used passwords, this can then be run by a computer against a login form to quickly try common passwords to gain access to an account. Brute force attacks are similar in that a computer can quickly try lots of combinations of letters and numbers. For example, a computer could try to figure out a password by trying all combinations of letters in the alphabet till the correct password is found. This is often stopped by websites limiting incorrect login attempts and having a long secure password that would even take computers billions of years to guess. Shorter, weaker passwords are most susceptible to brute force attacks.
Below we can see how long it would take to crack some common passwords and a completely random password created by a password manager.

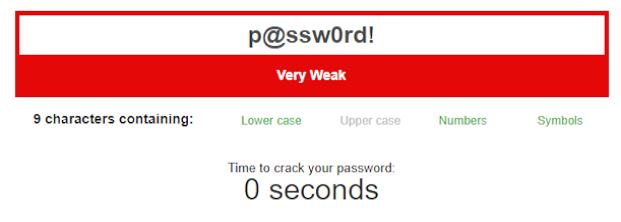
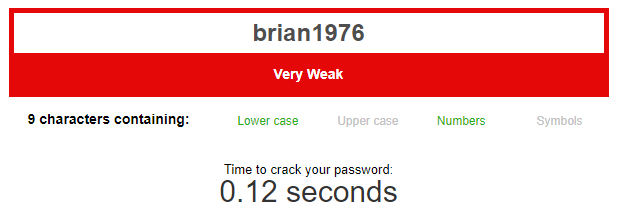

As you can see, the last password is 64 characters long and comprised of random characters and symbols. It would be incredibly hard to remember which is where the benefit of a password manager becomes so apparent. These passwords are very hard to crack and we can use a different, long, secure password for every website we use.
Most password managers also have features to help detect passwords you are using that have been involved in breaches and also pre-fill these into login prompts in your browser, making it extremely easy to log in even if you have a complex password.
Two Factor Authentication
Two factor authentication is another method that should be used (by default/habit) to secure our accounts. This allows us to help protect accounts even if an attacker can get hold of our password. Two factor authentication commonly works by asking the user to enter a code from their phone (authenticator application, SMS). It is likely that you already doing this with some accounts that enforce this feature by design, like your online banking.
Three things make up two factor authentication:
- Something you know - Such as a password or PIN.
- Something you have - Such as a device or security key.
- Something you are - Such as facial recognition or a fingerprint.
As you may have guessed with two factor authentication, you need at least two of these things to be able to access your account. As mentioned, most sites do this by having an app on your phone generate an OTP (One Time Passcode) which you are prompted to enter after entering your username and password. This password is “something you know” and your mobile phone with an OTP app is “something you have”.
Some password managers also allow OTP generation within them, ultimately removing the need for a separate device. This is great for convenience, but in the unlikely event someone was able to get into your password manager, then two factor authentication would not save your accounts. Using two factor within a password manager is better than not using it, but having your two factor on a completely separate device is more secure.
Using both a password manager to create and store strong passwords and using two factor authentication on your accounts will majorly reduce the risk of compromise.
What About at Work?
This advice is not just for use at home. It’s also important for businesses to protect their accounts in the same way. Employees using weak passwords, and not using two factor authentication, can be a big risk to the business and can cause data loss or big financial loss.
From years working for an MSP help desk, Lewis has seen businesses lose hundreds of thousands of pounds to attacks, these normally work by attackers who find an employee working in finance and looking for leaked credentials online, or simply try weak passwords to get into their business email account. An important thing to note is that if the user had two factor authentication enabled and set up, this attack could end here. Having gained access, the attacker would then email internally or send an invoice to a client with the attacker’s bank details asking for it to be paid.
Often attackers would get into the mailbox and monitor it for months to see who the user emails, what sort of conversations happen and the amounts of money being invoiced to make their attack as convincing as possible. Some attackers will even try to mimic the language and small details the user normally does in their emails to help convince the targets.
We highly recommend all businesses educate their users on general good security practices. This can be done with user training on password management, as well as two factor authentication and how to avoid phishing scams. In addition, providing employees with a password manager and training to use it so there is no excuse for weak passwords to be used in the organisation. This allows strong password policies to be enforced within applications and work environments, and ensures that employees will be able to adhere to them.
Business Password Policies
Businesses should, where available, set password policies to ensure users adhere to passwords that meet good practice standards. This helps stop users from setting weak passwords that could put the business at risk, this is important on all systems both externally and internally.
In the past, password policies would require users to change passwords after a set amount of days, generally about once a month. Research shows that most credentials are abused by attackers almost immediately and having users change their passwords regularly can make accounts less secure. It is now recommended, and best practice, to not require users to regularly change their passwords as it leads to users creating easier to remember passwords, or just slightly changing their old ones. This has its benefits as users can generate secure passwords from the start. This is of course less of an issue with a password manager, as the user does not need to remember the password altogether.
Password policies should still be in place to make sure user passwords meet certain criteria so the organisation can make sure weak passwords aren’t set by users. The NCSC requires the following for meeting the Cyber Essentials standard which is good advice to follow and a certification all organisations should aim to achieve:
- Using multi-factor authentication
- A minimum password length of at least 12 characters, with no maximum length restrictions
- A minimum password length of at least 8 characters, with no maximum length restrictions and use automatic blocking of common passwords using a deny list Read more on cyber essentials standards for password policies here.
We’ll be covering more on business security and best practices in posts to come, stick around and let us know if there is anything you’d like to see us cover.
You can contact us via email or X.
What Password Manager to Use?
Password managers have a range of ways they protect your data and it ranges from product to product. They also have different features and pricing which might help make the choice easier especially for business if you want features like AD/Azure AD integration or SSO (Single Sign On) support.
We don’t have any favourites here, but we do both use 1Password. Here is a list of options you can explore if looking for a password manager.
https://1password.com/ (Cloud hosted)
https://www.lastpass.com/ (Cloud hosted)
https://bitwarden.com/ (Cloud hosted and self hosted option) Self hosted option here https://bitwarden.com/help/self-host-an-organization/ Make sure to keep backups and protect your data.
https://www.dashlane.com/ (Cloud hosted)
https://keepass.info/ (Local offline) Make sure to keep backups and protect your data.
Further Reading
NCSC - Password expiry advice
https://www.ncsc.gov.uk/blog-post/problems-forcing-regular-password-expiry
NCSC - Cyber essentials requirements for infrastructure (Password policy requirements)
https://www.ncsc.gov.uk/files/Cyber-Essentials-Requirements-for-Infrastructure-v3-1-January-2023.pdf
NCSC - Using a password manager
https://www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online/password-managers
NCSC - Password manager buyers guide
https://www.ncsc.gov.uk/collection/passwords/password-manager-buyers-guide
NCSC - Activating two step verification
https://www.ncsc.gov.uk/collection/top-tips-for-staying-secure-online/activate-2-step-verification-on-your-email