This post is aimed at addressing what phishing attacks are, the damage they can do, and how to spot them. Phishing attacks are very common and apply to everyone. It’s important to know they can target you in your personal life and in work.
What Is A Phishing Attack?
Phishing attacks are when attackers attempt to trick victims into providing sensitive information through various means. They can range from simple emails pretending to be someone such as a colleague, or friend, through to sophisticated attacks where attackers will register domains and clone websites to try and steal login information.
To help visualise what some different phishing attacks might look like, lets see some examples of phishing attacks.
Spear & Whaling phishing attack
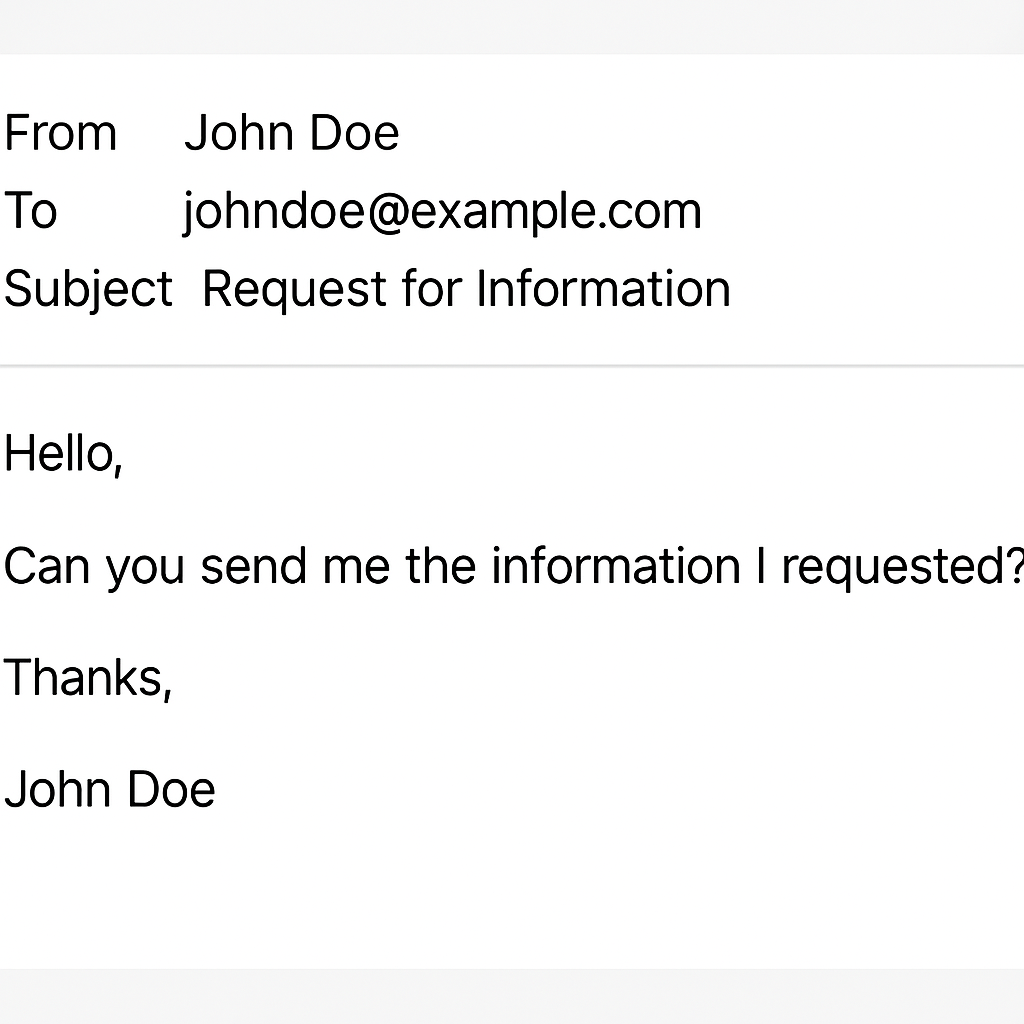
A basic phishing email could look something like the above, commonly sent from an attacker pretending to be a friend, or co-worker. This could be used to obtain specific information such as invoices and company details that can be used in further attacks. A commonly seen attack in this style is that of a CEO asking for information, or a payment to be sent urgently. This can be sent from a compromised mailbox on a legitimate address or via a email account registered for the attack and made to look as close to the real account as possible. Spear phishing attacks normally already have some information such as the names of co-workers, your job role etc to tailor the attack. This would require the attacker to perform some prior research, such as Open Source Intelligence (OSINT) gathering, in an attempt to help the emails and phishing requests look legitimate.
Similar to spear phishing attacks, there are whaling attacks. Although similar, these focus of phishing high profile individuals such as the directors of a company. Normally the attacker would attempt to gain information by impersonating trusted partners, or IT departments, to gain the users trust and have them perform the wanted actions.
Clone Phishing attack
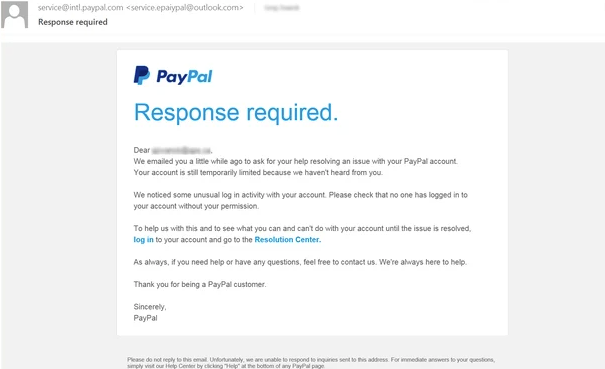
In this type of phishing attack, the attacker is normally attempting to obtain login information for an account. For example, they could pretend to be a bank, or social network website, claiming there is a problem with your account and providing a link to resolve the issue. In this case, the link would redirect the unsuspecting user to a cloned page which the attacker controls. Any information that is input into the cloned page would be sent to the attacker. We can see in the example above that the attacker has created an email to look like it’s from PayPal. The two links in this email redirect to a fake PayPal login page created by the attacker to harvest login information. Normally, when logging into a fake website, the page could produce a pop saying “wrong credentials” and then reload the real website in attempt to hide the malicious activity that just occurred.
SMS Phishing (Smishing)
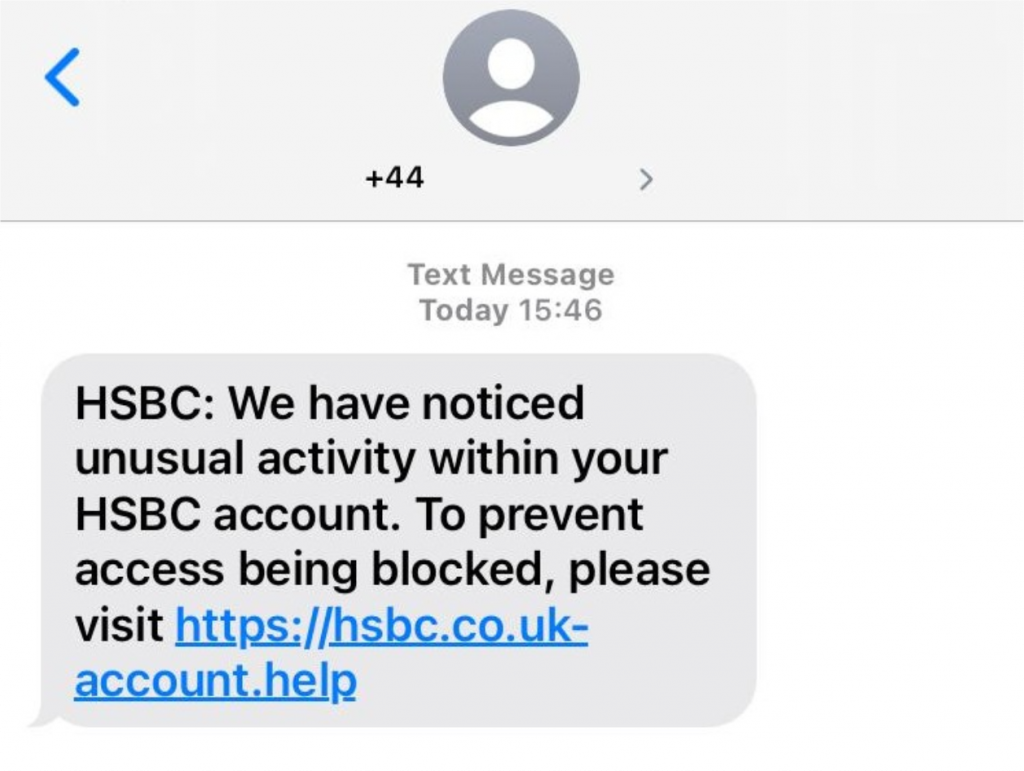
Phishing is not only done via email. Some attackers will use SMS to send phishing attacks directly to the target’s mobile phone number. It’s likely you will have had one of these in the past. They work largely the same as email based phishes, but are sent over SMS or a messaging service, such as WhatsApp. These commonly revolve around an account being locked, or some urgent problem that needs to be resolved immediately to help persuade the user to click the link. This will again go to a page controlled by the attacker to harvest information such as card or login details, depending on the impersonated service.
Vishing (voice phishing)
Similar to smishing, vishing is a phishing attack but via a voice call. This is normally an attacker pretending to be a government authority, or bank, in order to try and scam users out of information or money. It’s very likely you have received one of these types of calls where someone on the other end is telling you that you might owe an amount of tax and that you could face a huge fine/prison if you do not resolve it immediately on the phone. These are designed to instil panic and fear so the target acts straight away.
Angler phishing
Angler phishing is when an attacker impersonates a brand on a social media platform, such as Facebook or X. They then use the account to pretend to be a brand and interact with existing users/customers of the brand or potential new customers. This is normally done with “support” accounts to take advantage of target users that might be trying to complain, or are having issues with a real paid service/product.
How To Identify A Phishing Attack
Now we know the types of common phishing attacks, the important question is “how do we avoid them?” Whilst email services are getting better at detecting and blocking phishing emails, an important preventative measure against them is user training. It’s important that users are aware of phishing attacks and what to look out for, so they can ultimately be detected and blocked.
For email based phishing attacks there are some things we can check to determine if an email is legitimate. This includes:
- The senders email address: First of all, is the email address correct? Or if the email claims to be from a reputable source, such as a company, is the email using a known company domain. Is that domain letter for letter perfect with regards to the official company website, or other previous emails you may have received from them.
- Suspicious links or attachments: does the email contain links or attachments you don’t recognise? You should always be careful of attachments and links you are not sure about. If you have received a download, or similar, from someone you don’t know, it’s important to be cautious. In addition, it’s also important to remember that hyperlinked text (links) might not be targeting the same website as to the one displayed. This is presented in the screenshot below. If you get an email from what appears to be a trusted source asking you to log in to a service, it’s worth navigating to the website directly with the known domain rather than clicking a link within a received emails.
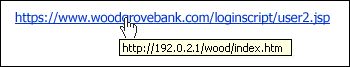
- Time sensitive actions: Does the email contain an urgent call to action? Phish emails often attempt to have the user preform actions urgently by invoking fear into the reader. If an email is asking for a link to be clicked urgently, or some other form of user action, it’s definitely worth checking the legitimacy before acting out of fear.
- Bad spelling and grammar: Does the email contain bad grammar or incorrect spelling? Phish emails can often have bad spelling and grammar. Remember, most companies will spellcheck their email content before sending as to help maintain a reputation and professional appearance. Nefarious actors won’t really care, they just want to you to click the link.
There are many clues an email might be a phishing attempt, and although email providers are getting better at detecting and blocking phishing emails, it’s always good to double check suspicious emails just to be sure. It’s wise to not click links or open attachments from any email unless you 100% trust the sender.
If you work for a company, and have an IT department that help support and handle your internal company emails, check to see if there is a spam/suspicious inbox you can forward emails to, allowing further analysis to be performed safely. This will hopefully help protect colleagues from receiving/falling for these attacks if the attackers change targets.
What To Do If You Fall For A Phishing Attack..
Sometimes phishing attacks are easy to spot and sometimes they’re cleverly designed attacks that get us when we’re rushed and might miss the common signs. At the end of the day, we are all human and mistakes happen. In the event you do fall for a phishing attack, it’s important to act fast. Depending on the type of attack will determine the action you should take. For example, if you give payment details to the attacker it’s vital that you contact your banks fraud team and seek their advice. This will likely involve replacing the card, but work quickly before purchases can be made by the attacker and your money stolen.
If you have given away login details for a specific website, it’s important to change those credentials before the attacker can. If these are part of your work or business login credentials, make your IT department aware as quickly as possible so they can take action and contain the attack. This could include temporarily restricting all access to your account until it is resolved. It’s also important to remember to change any other passwords that are the same as the one that is now compromised. This highlights the importance of a password manager, the issues with password re-use and enabling multi-factor authentication (MFA) on all accounts. We have a post digging more into this topic here.
Phishing attacks are very common, and many people fall for them. It’s important to be aware of these types of attacks and how to check for common signs. Most people will fall for phishing attacks at some point in their life, and many security professionals have also fallen for attacks. It’s good to know how to deal with attacks and what action to take so you can quickly limit the damage an attack could cause to ultimately help protect yourself and your assets.